'Google Domains' Starts Migrating to Squarespace
Read more of this story at Slashdot.
Read more of this story at Slashdot.
Read more of this story at Slashdot.
Read more of this story at Slashdot.
Read more of this story at Slashdot.
Read more of this story at Slashdot.
Minimachines.net en partenariat avec TopAchat.com
Les Bons Plans du Week-End : 18-20/05/2024 © MiniMachines.net. 2024.
Read more of this story at Slashdot.
Nous voilà bien.
J’avais dit que je teasais mon strip, mais je suis nul en pub et j’ai surtout bien d’autres choses à vous raconter cette semaine, notamment ces histoires de “Choose France“,
de parts de gâteaux culturels, de poisse de fusée, ou même encore de self-control.
En parlant de self-control, vu que j’en ai manqué, faut quand même que je vous raconte pour ce strip. J’étais au carrefour de la fin de semaine avec le weekend, quand voilà que déboule comme une furie un strip, sans crier gare, ni même claxonner. Il me semblait évident de devoir lui laisser la priorité. Du coup j’ai dû accélérer. Pardonnez les couleurs de signalisation et les traits en pointillé, au moins je n’ai quasiment pas dépassé les lignes blanches.
Mais pas d’inquiétude, j’étais en règle, ce strip est réglo, j’avais bien mes papiers : les voici, ici et ici.
Merci m’sieur l’agent !
Cette chronique est financée grâce au soutien de nos abonnés. Vous pouvez retrouver comme toutes les précédentes publications de Flock dans nos colonnes.
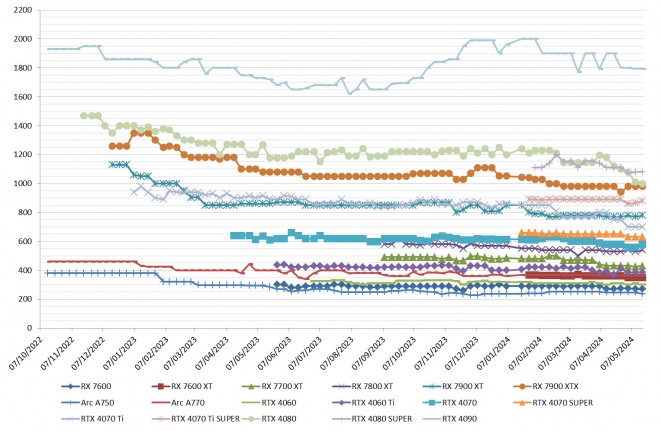
Autant le dire tout de suite ce n'est pas la fête des tarifs cette semaine... Chez AMD nous avons la 7700 XT qui augmente de 5 euros, la 7800 XT qui monte de 10 euros et la 7900 XT qui fait aussi + 10 euros cette semaine. Pour les autres références, pas de changement. Chez Intel, nous avons la A750 qui baisse de 10 euros, youhou !!! […]
Lire la suite
Deux vidéos ont été prduites par la team Cowcotland cette semaine. La première porte sur la découverte des vrais claviers mécaniques par Eldran. La seconde porte sur le premier boitier Cooler Master qui est compatible avec les cartes mères qui présentent des connecteurs arrière, le Masterbox 600. […]
Lire la suiteRead more of this story at Slashdot.
Read more of this story at Slashdot.
Read more of this story at Slashdot.